Blog written by Eide Bailly, a Greater Mankato Growth Bronze Investor
In today’s business environment, understanding your current security risks just makes sense. After all, studies have found that U.S. organizations face the highest costs when a data breach occurs, topping out at at $8.64 million per breach.
A proactive stance on cybersecurity risk can equate to major savings for organizations. A collaborative approach between security and networking has been shown to significantly lower the cost of a breach. In fact, organizations who formed incident response teams and tested their incident response plans were able to reduce the cost of a data breach by almost 40%.
So, if we know that a strategic approach that focuses on security processes and formal incident response leads to lower costs and less time lost, why don’t most companies do it?
It all begins with building a culture of security within your organization and understanding what that entails.
Defining a Culture of Security
You can’t talk about a culture of security without first understanding what cybersecurity is. Cybersecurity is the combination of people, processes, products and technology that protect you and your organization from cyberattacks. It’s a critical practice aimed at protecting your data and the sensitive information your clients entrust you to handle.
Cybersecurity is not about a specific tool or product. Rather, it’s a mindset shift within an organization. It’s moving from reactive to proactive.
Creating a culture of security is crucial to making sure your organization is implementing the necessary tools and processes to minimize risk. This culture is driven from the top down through executive decisions and internal promotion of effective cybersecurity processes and procedures.
Building this culture of security utilizes a practical, strategic approach. It’s an ongoing process with constant attention to potential threats and a focus on how to protect your company long-term.
Who is Responsible for a Culture of Security?
Ultimately, many organizations believe security lies within their IT department. However, culture isn’t set by the IT department. A true culture of security begins with a tone at the top.
Ask yourself:
- What steps have you taken to identify and protect your most valuable IT assets?
- What is your level of confidence that your business network(s) and data are secure?
- What are your biggest concerns related to IT security and cyberattacks?
Top-performing organizations seek to align their cybersecurity risks to overall business risks and objectives.
The Five Stages of Cybersecurity
As a leading cybersecurity consulting firm, we’ve seen our fair share of effective and ineffective security practices. Here are the five stages we recommend as organizations create comprehensive, in-depth cybersecurity action plans.
- Stage 1: Foundational Security
- Stage 2: Policies and Awareness
- Stage 3: Key Processes
- Stage 4: Incident Preparedness
- Stage 5: Security Monitoring
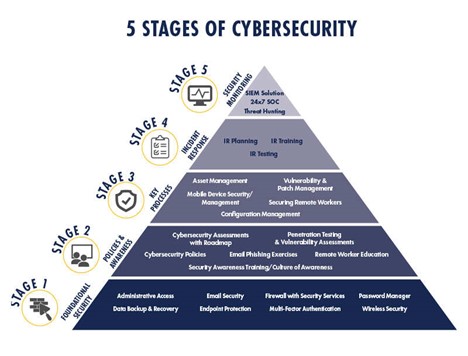
While each has their own unique benefits, a true culture of security relies on each stage working together for peak efficiency and protection.
Need a cybersecurity check for your organization?
Here’s What a Culture of Security Looks Like in Detail
Stage 1: Foundational Security
The best plans begin with the proper foundation. Stage 1 assesses basic functions within your organization and common entry points for potential cyberthreats, providing an ongoing “health check” for your IT.
From your processes to your tools, network, and security practices, smart business is all about adapting to change and remaining secure. Because the last thing you want to do is leave yourself—and your data—out in the open.
To begin, ask questions like:
- What are some best practices that I can enforce in my organization?
- How do I measure my current security risk?
- Where should I focus my energy?
Next, identify where your critical data and assets are within your network and how they are accessed. This includes things like:
- Administrative Access
- Data Backup & Recovery
- Email Security
- Endpoint Protection
- Network Security (Firewall, IDS/IPS, etc.)
- Multi-factor Authentication
- Password Manager
- Wireless Security
Stage 2: Policies and Awareness
Once the foundation is laid, it’s time to set up the policies you need to keep things running efficiently and securely. This includes an acceptable use agreement and a writeup of company cybersecurity policies. This should include disaster recovery, business continuity and work from home standards, among others.
Creating a culture of cybersecurity involves more than just creating policies; organizations need to make sure the individuals utilizing them understand the “why.” Awareness and continual education will be vital to the success of your policies. After all, attentiveness to cybersecurity risk in the workplace really is everyone’s business.
From security training to email phishing exercises and remote worker education, it’s important to prepare and educate your staff, as they have the greatest ability to expose your organization and leave it more vulnerable to cyberattacks.
Stage 3: Key Processes
Now that you’ve checked your current systems and have proper education in place for your people, it’s time to align key processes.
Ideally, these processes will center around areas where your organization has exposed vulnerabilities and increased risk.
Typically, these include:
- Asset Inventory
- Mobile Device Security
- Patch Management
- Security for Remote Workers
- Standard Configuration
You should also set up regular processes for vulnerability scanning. Cybersecurity risk is ongoing, so processes must be routinely updated to address the ever-changing threat landscape.
Stage 4: Incident Preparedness
There is always potential for an incident to occur, and the worst time to plan is during or after the incident. Preparation is critical to minimizing the impact of an incident and essential for building a culture of security. Integrating proper systems, processes, and awareness practices can lead to lower downtime and lessen the financial impact of an incident.
Creation and implementation of a proactive incident response plan is vital to the success of recovering. Incident response is how you respond to an attack when it happens. The primary goal of incident response is to minimize damage by quickly responding to an incident while preserving necessary evidence to prevent future attacks.
An incident response plan does not have to be lengthy or overly complex. An ideal incident response plan should:
- Define what an incident is
- Identify who is responsible (both internally and externally) for assisting in response to an incident
- Outline the process of identifying and responding to potential incidents
A strong, well-documented incident response plan makes for better prepared organizations. In fact, NetDiligence’s Cyber Claims Study Report notes that incident response preparedness saved organizations $2 million on average.
Once a plan is in place, it is best to exercise your plan to identify gaps and efficiencies that can be made. Doing so prepares the teams involved to respond quickly and effectively to an incident.
Stage 5: Security Monitoring
The last stage focuses on ongoing support. After all, maintaining a culture of security is a constant process.
A few ways companies can ensure security monitoring include:
- SIEM Solution: A SIEM aggregates the log data from various services (e.g., endpoints, anti-virus, firewall, etc.) and can correlate events to provide better visibility of activity within your network.
- 24/7 SOC (Security Operations Center): Analysts constantly monitor for and respond to anomalies identified within your network.
- Threat Hunting: Searching your network for common attack tactics and indicators of compromise.
- Managed Security Service Providers (MSSPs): Offloading the monitoring and hunting in your environment to a third party to manage your security stack. MSSPs only present relevant data to organizations so they can focus on what really matters.
How to Establish a Culture of Security
Establishing a culture of security begins with a top-down approach that aligns cybersecurity risk with business goals. It’s more than just protecting your systems and data—it also involves proactive processes that focus on security basics and continual education. Cybercriminals are relying on human error and fear to help them gain access. Proper preparation and vigilance within your cybersecurity program will have the greatest impact in preventing successful attacks.
Cybersecurity is the combination of people, processes, products and technology that protect you and your organization from cyberattacks. It’s a critical practice aimed at protecting your data and the sensitive information your clients entrust you to handle.
Cybersecurity is not about a specific tool or product. Rather, it’s a mindset shift within an organization, moving from reactive to proactive.
Creating a culture of security is crucial to making sure your organization is implementing the necessary tools and processes to minimize risk.





